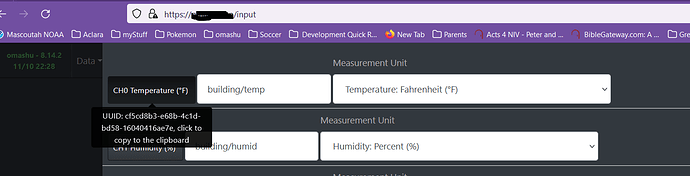
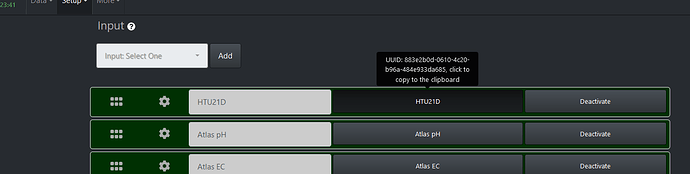
Working fine over here. It’s likely you’re passing an invalid parameter in the URL. The Web log should indicate the issue.
user@dev:~ $ curl -k -v "https://192.168.0.26/api/measurements/past/883e2b0d-0610-4c20-b96a-484e933da685/C/0/360" -H "authorization: Basic MYAPIKEY" -H "accept: application/vnd.mycodo.v1+json"
* Trying 192.168.0.26:443...
* Connected to 192.168.0.26 (192.168.0.26) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/certs/ca-certificates.crt
* CApath: /etc/ssl/certs
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.3 (IN), TLS handshake, CERT verify (15):
* TLSv1.3 (IN), TLS handshake, Finished (20):
* TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.3 (OUT), TLS handshake, Finished (20):
* SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384
* ALPN, server accepted to use http/1.1
* Server certificate:
* subject: O=mycodo; OU=mycodo; CN=mycodo
* start date: Jul 15 02:18:32 2022 GMT
* expire date: Jul 15 02:18:32 2032 GMT
* issuer: O=mycodo; OU=mycodo; CN=mycodo
* SSL certificate verify result: self signed certificate (18), continuing anyway.
> GET /api/measurements/past/883e2b0d-0610-4c20-b96a-484e933da685/C/0/360 HTTP/1.1
> Host: 192.168.0.26
> User-Agent: curl/7.74.0
> authorization: Basic 5VE2Mnm501mf3zB1qdwBDChFUXxUhzd6rLkIcbaPvg6lfG5Nlyh0oebgcrNFBXa1oqyMVzpcWrW3o4A5KzuKo00Yr8SwkUbr49p4YTgNefE6ocx3LM2xk1HrTPLLEloxJozdbb1ImLTXD1zDFaOWh9zSJGjWluLRAyXZPstTc50=
> accept: application/vnd.mycodo.v1+json
>
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* old SSL session ID is stale, removing
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Server: nginx/1.18.0
< Date: Thu, 10 Nov 2022 23:26:15 GMT
< Content-Type: application/vnd.mycodo.v1+json
< Content-Length: 1305
< Connection: keep-alive
< X-Frame-Options: SAMEORIGIN
< X-XSS-Protection: 1; mode=block
< X-Content-Type-Options: nosniff
< Content-Security-Policy: default-src * 'unsafe-inline' 'unsafe-eval'
< Strict-Transport-Security: max-age=31556926; includeSubDomains
< Referrer-Policy: strict-origin-when-cross-origin
< X-RateLimit-Limit: 200
< X-RateLimit-Remaining: 199
< X-RateLimit-Reset: 1668122836
< Retry-After: 60
< Vary: Accept-Encoding
< Set-Cookie: session=78d104f5-b9bf-4e45-8cb4-12abba8aad32; Expires=Sun, 11 Dec 2022 23:26:15 GMT; Secure; HttpOnly; Path=/; SameSite=Lax
<
{"measurements":[{"time":1668122422.459048,"value":23.335039062499995},{"time":1668122437.485661,"value":23.324313964843746},{"time":1668122452.494764,"value":23.324313964843746},{"time":1668122467.515885,"value":23.313588867187498},{"time":1668122482.485509,"value":23.324313964843746},{"time":1668122497.553354,"value":23.335039062499995},{"time":1668122512.52341,"value":23.345764160156243},{"time":1668122527.4897,"value":23.345764160156243},{"time":1668122542.439131,"value":23.335039062499995},{"time":1668122557.550108,"value":23.335039062499995},{"time":1668122572.499873,"value":23.324313964843746},{"time":1668122587.495814,"value":23.335039062499995},{"time":1668122602.465043,"value":23.345764160156243},{"time":1668122617.571325,"value":23.35648925781249},{"time":1668122632.492514,"value":23.345764160156243},{"time":1668122647.445638,"value":23.367214355468754},{"time":1668122662.507987,"value":23.377939453125002},{"time":1668122677.4636,"value":23.367214355468754},{"time":1668122692.571492,"value":23.345764160156243},{"time":1668122707.546087,"value":23.367214355468754},{"time":1668122722.509666,"value":23.35648925781249},{"time":1668122737.503587,"value":23.377939453125002},{"time":1668122752.505009,"value":23.38866455078125},{"time":1668122767.510216,"value":23.3993896484375}]}
* Connection #0 to host 192.168.0.26 left intact